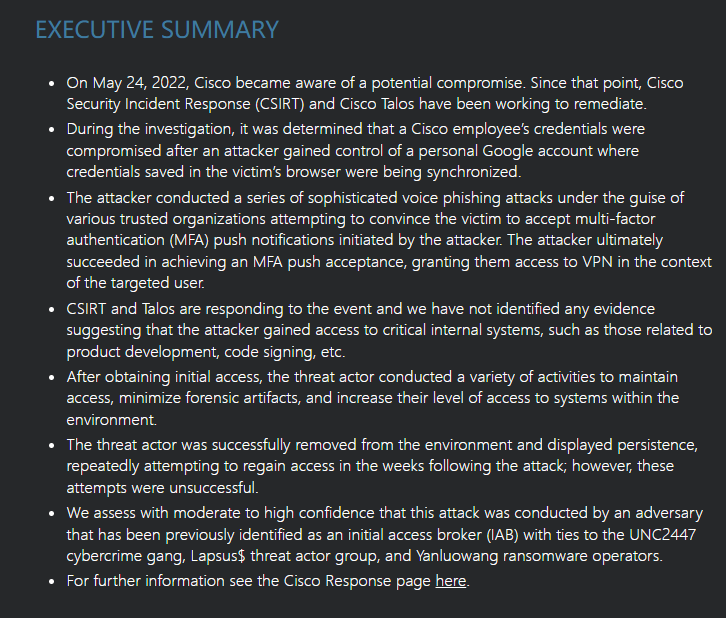
The networking giant Cisco Systems Inc. acknowledged last Wednesday that it was attacked by UNC2447, Lapsus$ and, Yanluowang (Demon) ransomware groups on May 24, 2022, and allegedly lost a total of 2.75 gigabytes of data.
Cisco Security Incident Response Team (CSIRT) and risk intelligence branch Cisco Talos clarified that Cisco didn’t detect any impact to its business or related services, sensitive customer or employee data, or supply chain activities because of the hack.
Phishing attack employee credentials to access internal network
Yanluowang group stole employee’s credentials to get access to Cisco’s system by hijacking their Google accounts, which comprised credentials synchronized from the browser.
Through MFA fatigue and voice phishing attacks by the threat actors impersonating trusted sources, the attacker persuaded Cisco employee to accept multi-factor authentication (MFA) push alerts.
MFA fatigue is an attack strategy where criminal groups pester a target with a persistent barrage of requests in the hopes that they finally accept one to prevent them. After ultimately tricking the victim into receiving one alert, Yanluowang was able to connect to the VPN in the disguise of targeted user.
The gang managed to spread to Citrix servers and domain controllers, and while they escalated to administrative privileges, their actions alarmed CSIRT and were expelled at last.
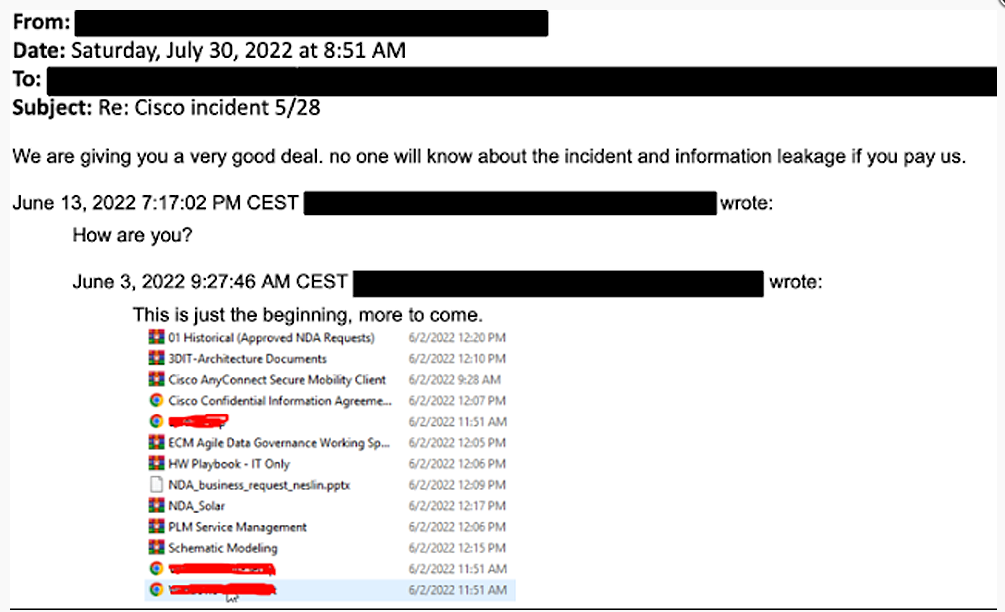
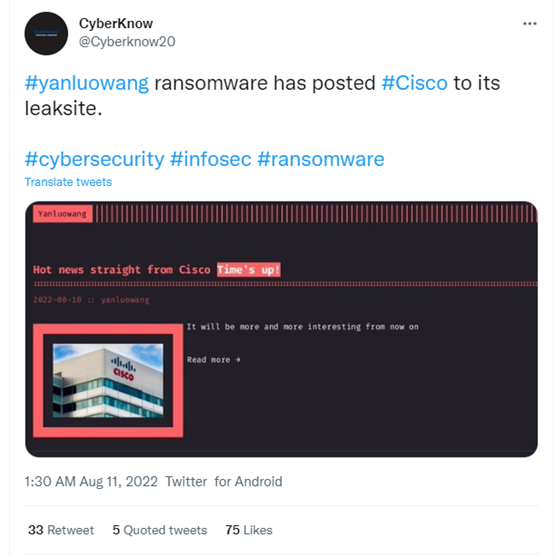
Hackers claim to obtain Cisco data and ask for ransomware
How to Prevent Ransomware?
Ransomware attacks are everywhere, and they are huge threats for data security. However, they are not undefeated. A comprehensive, all-hands-on-deck strategy involving your entire organization is needed to combat ransomware.
Establish a response plan: Create an incident response strategy to ensure that your IT security staff is prepared for a ransomware outbreak or other kinds of cyber attacks. The strategy should specify the communications channels and responsibilities that will be used during an attack. A list of contacts, such as any partners or vendors who need to be contacted, should also be included.
Strengthen your endpoints: The threat surface of your business can be reduced with the aid of secure configuration settings, which can also patch any security holes left by default setups. And keep the systems, software, and firewalls updated to help close the security gaps.
Maintain backups constantly: Backing up crucial data is the most effective way of recovering from cyber attacks. You need to make sure safety of your Hyper-V Backup solutions, though. Either you store them in remote sites with multiple copies or you put them on the cloud to mitigate the ransomware attacks.
Vinchin Backup & Recovery is a virtual data protection for 10+ virtualizations that keeps frequent and fast backups with data reduction technologies and CBT/SpeedKit technology via multithreaded transmission, and secure them with a real time IO denying any unauthorized access to prevent malware or ransomware. There are 15s instant recovery and offsite backup copy to safeguard data security and business continuity if something happens.
You can download the 60-day free trial of Vinchin Backup & Recovery now to protect your crucial data now.